Seidat Data Processing Addendum (DPA)
This Data Processing Addendum (“DPA”) forms part of Seidat’s Terms of Service, which are available on this page between Seidat and the Customer (the “Agreement“) under which Seidat provides its Software-as-a-Service (“Product“, “Service“, or “Application“).
1. Definitions
Terms not specifically defined herein shall have the meaning set forth in the Agreement.
1.1. “Data Controller” means the legal entity which, alone or jointly with others, determines the purposes and means of the Processing of Personal Data.
1.2. “Data Processor” means the legal entity that Processes Personal Data on behalf of the Data Controller.
1.3. “Data Protection Laws” means GDPR.
1.4. “Data Subject” means an identifiable natural person to which the Processing of Personal Data is related.
1.5. “EEA” means the European Economic Area.
1.6. “GDPR” means the General Data Protection Regulation (EU) 2016/679.
1.7. “Personal Data” means Personal Data relating to a Data Subject as an identified or identifiable natural person. An identifiable natural person is one who can be identified, directly or indirectly, by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural, or social identity of that natural person.
1.8. “Personal Data Breach” means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, Personal Data transmitted, stored or otherwise Processed.
1.9. “Processing or Process” means any operation or set of operations performed on Personal Data or sets of Personal Data, such as collecting, recording, organizing, structuring, storing, altering, retrieving, consulting, using, disclosing by transmission, disseminating, or otherwise making available, aligning or combining, restricting, erasing or destroying.
1.10. “Subprocessor” means a third party engaged by Seidat as a Data Processor under this DPA.
1.11. “Third Country” means a country outside the EEA that is not recognized by the European Commission as providing an adequate level of protection for Personal Data pursuant to GDPR.
2. Processing of Personal Data
2.1. Scope and roles of the parties. This DPA applies to Seidat’s Processing of Personal Data by virtue of providing the Service to the Customer. For the purposes of this DPA, the Customer is the Data Controller, and Seidat is the Data Processor Processing Personal Data on the Customer’s behalf.
2.2. Purpose and duration of the Processing. Seidat will Process Personal Data to provide the Service. The duration of Processing of Personal Data shall be for the term of the Agreement.
2.3. Types of Personal Data and categories of Data Subjects. The types of Personal Data and categories of Data Subjects are set forth in Appendix 1 below.
2.4. Instructions for Processing. Seidat shall Process Personal Data in accordance with the Customer’s documented instructions, including with regards to transfers of Personal Data to a Third Country. The Customer instructs Seidat to Process Personal Data to provide the Service in accordance with the Agreement and this DPA. Seidat may Process Personal Data otherwise than on the Customer’s instructions if requested to do so by applicable law. Seidat will in such case inform the Customer of that legal requirement before Processing unless that law prohibits such information on important grounds of public interests.
2.5. Seidat personnel. Seidat ensures that all personnel authorized to Process Personal Data are subject to a perpetual confidentiality obligation, and that such personnel receive appropriate training on their responsibilities regarding the Processing and safeguarding of Personal Data pursuant to applicable Data Protection Laws. Authorized personnel shall only be granted access to Process Personal Data to the extent strictly necessary to carry out the Agreement. Seidat follows an annual training plan for all of its employees.
2.6. Return and deletion of Personal Data. Seidat shall return on request and delete Personal Data in accordance with the Agreement upon termination of the Agreement. The terms of account deletion are described in Seidat Terms of Service under “Cancellation and Termination”. Seidat shall confirm upon written request from the Customer that such return and deletion has been conducted.
2.7. Compliance with laws. Seidat shall comply with all Data Protection Laws applicable to Seidat in its role as a Data Processor Processing Personal Data. The Customer shall comply with all Data Protection Laws applicable to the Customer as a Data Controller.
3. Subprocessors
3.1. Authorization to engage Subprocessors. Seidat may engage Subprocessors to provide certain services on its behalf. The Customer authorises Seidat to engage the Subprocessors listed in Appendix 2. Seidat may replace or engage new Subprocessors.
3.2. Notifications of updates and possible objections: Seidat has a mechanism to subscribe to receive notifications about the addition of Subprocessors available on its Data Processing Addendum (DPA). To subscribe to receive notifications, visit here: https://www.seidat.com/subprocessor-notifications/. Seidat will provide such notification to those email addresses that have subscribed at least fourteen (14) days in advance of allowing the new Subprocessor to Process Personal Data (later: the “Objection Period”).
3.2.1. During the Objection Period, objections (if any) to Seidat’s appointment of the new Subprocessor must be provided to Seidat in writing and be based on reasonable grounds. In such an event, the Parties will discuss those objections in good faith to achieve resolution.
3.2.2. If it can be reasonably demonstrated to Seidat that the new Subprocessor is unable to Process Personal Data in compliance with the terms of this DPA and Seidat cannot provide an alternative Subprocessor, or the Parties are not otherwise able to achieve resolution, Customer, as its sole and exclusive remedy, may terminate the applicable Subscription in accordance with the process laid in the Agreement only with respect to those aspects which cannot be provided by Seidat without the use of the new Subprocessor. Seidat will refund the Customer any prepaid unused fees for such Subscription following the effective date of such termination.
3.3. Adding a new Subprocessor to this DPA does not trigger a re-acceptance of the Seidat Terms of Service.
3.4. Subprocessors’ compliance. Seidat is fully responsible for its Subprocessors’ compliance with this DPA. Seidat shall conclude a written agreement with each Subprocessor.
-
-
- (i) making the Subprocessor subject to at least the same level of data protection as imposed on Seidat in this DPA, and
- (ii) restricting the Subprocessor from Processing Personal Data for any other purpose than delivering the contracted services.
-
4. Rights of Data Subjects
4.1. Requests from Data Subjects. The Customer is responsible for responding to Data Subjects’ requests for access, correction, deletion, or restriction of that person’s Personal Data. If Seidat receives a request from a Data Subject, Seidat shall promptly redirect the Data Subject to the Customer.
4.2. Seidat’s assistance. Seidat shall comply with Customer’s reasonable requests on behalf of Data Subjects pursuant to Data Protection Laws to (a) correct, delete, or restrict Processing of Personal Data, (b) make available Personal Data and associated Processing information, and (c) to enable data portability of a Data Subject’s Personal Data if alternative (a), (b) or (c) is not feasible to the Customer through the Service. Seidat may charge the Customer for reasonable costs inflicted on a time and material basis for assistance according to this Section.
5. Security of Personal Data
5.1. Security of Processing. Seidat shall implement and maintain appropriate technical and organizational measures to protect Personal Data against accidental or unlawful destruction, loss, alteration, unauthorized disclosure, or access. Seidat shall ensure a level of security appropriate to the risk, including encryption of Personal Data to ensure ongoing confidentiality, integrity, availability, and resilience of Seidat’s Service and associated systems.
5.2. Personal Data Breach. Seidat shall without undue delay notify the Customer when becoming aware of a Personal Data Breach. Such notification shall describe
-
-
-
- (i) the nature of the Personal Data Breach,
- (ii) the details of a contact point where more information concerning the Personal Data Breach can be obtained,
- (iii) the Personal Data Breach’s effect and consequences for the Service,
- (iv) and the measures taken or proposed to be taken by Seidat to address the Personal Data Breach, including measures to mitigate its possible adverse effects.
-
-
Seidat shall cooperate with and assist the Customer in preventing, mitigating, and rectifying a Personal Data Breach in accordance with applicable Data Protection Laws considering the nature of the Processing and the information available to Seidat. Seidat may charge the Customer for reasonable costs on a time and material basis for any assistance related to Personal Data Breach under this Section unless Seidat must be deemed responsible for the cause initiating the activity
5.3. Data Protection Impact Assessments and prior consultations. Seidat shall provide reasonable assistance to the Customer to carry out a data protection impact assessment and prior consultation with the supervisory authority related to the Customer’s use of the Service. The customer is entitled to use Seidat’s audit reports when conducting such activities imposed by Data Protection Laws, including GDPR Article 35 and 36. According to this Section, Seidat may charge the Customer for reasonable costs inflicted on a time and material basis based on assistance.
5.4. Audit. Seidat shall make available to the Customer all information necessary to demonstrate compliance with this DPA. The information is subject to Customer’s confidentiality as stipulated in the Agreement. If the Customer requires additional information, the Customer may conduct an audit by engaging an independent, qualified third party to conduct such audit. Any such audit shall follow Seidat’s reasonable security requirements and not interfere unreasonably with Seidat’s business activities. The Customer shall give Seidat 14 calendar days prior written notice before any audit can be initiated. All costs relating to the audit shall be compensated by the Customer.
5.5. Notification of unlawfulness. Seidat shall immediately inform the Customer if it considers that its Processing of Personal Data pursuant to this DPA violates applicable Data Protection Laws. The Customer is in such case entitled to suspend any further Processing of Personal Data until Seidat has conducted necessary corrections.
6. Miscellaneous
6.1. Liability. Each party’s liability under this DPA is governed by the Agreement unless otherwise required by applicable Data Protection Laws.
6.2. Affiliates of Customer. The Customer is responsible for coordinating all communication with Seidat on behalf of its Affiliates regarding this DPA. The Customer represents that it is authorized to issue instructions as well as make and receive any communications or notifications in relation to this DPA on behalf of its Affiliates.
6.3. Termination. The term of this DPA will end upon termination of the Agreement.
6.4. Conflict. In the event of inconsistencies between the provisions of this DPA and the Agreement, the provisions of this DPA shall prevail regarding the parties’ data protection obligations.
7. Appendix
7.1. Appendix 1 – Types of Personal Data and Categories of Data Subjects
7.1.1. Types of Personal Data. The types of Personal Data processed under this DPA include any Personal Data uploaded to the Service by the Customer.
7.2.2. Categories of Data Subjects. The Data Subjects may include Customer’s customers, employees, suppliers, and end users, or any other individual whose Personal Data the Customer uploads to the Service.
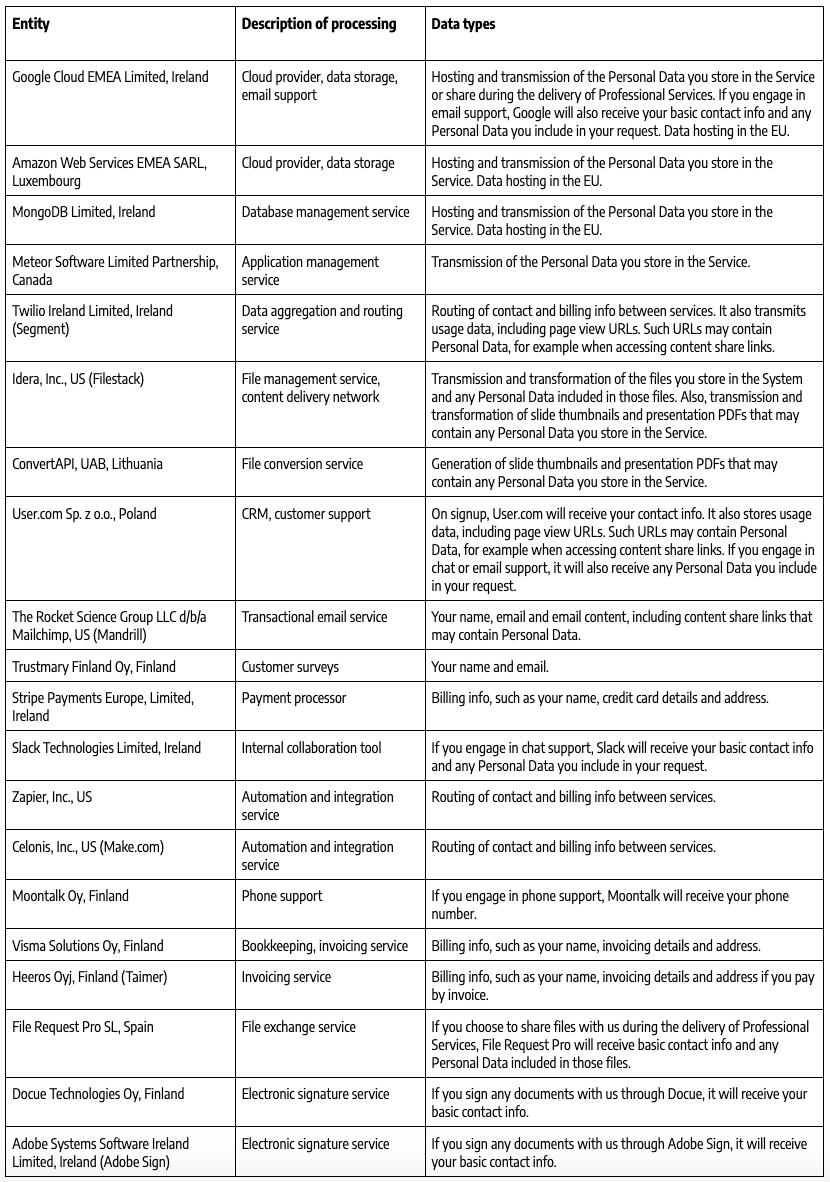
7.2. Appendix 2 – List of Subprocessors
7.3. Security Measures
7.3.1. Access control and measures for user identification and authorization for Seidat personnel. Seidat has implemented a robust access control system to ensure that only authorized Seidat personnel have access to Personal Data. Access to Personal Data is limited to authorized personnel who require access for support purposes only.Seidat uses a range of measures to ensure user identification and authorization, including user authentication, two-factor authentication, and single sign-on. Unique login credentials are required for all users, and access to Personal Data is granted based on the user’s role and level of authorization, ensuring that users only have access to the data necessary for their job functions. All user accounts are monitored, and we conduct regular reviews of user access privileges to ensure that only authorized individuals have access to Personal Data.All Seidat personnel authorized to access Personal Data are trained to comply with applicable Data Protection Laws and are subject to a perpetual confidentiality obligation applicable to their support work.
7.3.2. Data encryption and pseudonymization. Seidat uses industry-standard encryption technologies to secure data both in transit and at rest.
7.3.3. Data storage and retention. We act appropriately to ensure that the Customers’ data is stored and retained in a secure manner. The Customers’ data is logically separated from system- and application data and other Customers’ data, with access controls and monitoring mechanisms in place. We also regularly test, assess, and evaluate the effectiveness of our technical and organizational measures to ensure the security of the Processing.Seidat has implemented measures to ensure the availability and access to Personal Data in the event of a physical or technical incident.In addition to these measures, Seidat maintains disaster recovery and business continuity plans that are designed to ensure that we can respond quickly and effectively in the event of a disruption or outage. Our plans include procedures for restoring access to personal data, identifying and mitigating potential risks, and communicating with customers and other stakeholders in a timely and transparent manner.
7.3.4. Certifications. Seidat aims to obtain the ISO 27001 certification, which demonstrates our commitment to information security management. We will regularly undergo audits and assessments to maintain this certification, ensuring our compliance with applicable Data Protection Laws.
7.3.5. Physical security. Seidat acts appropriately to ensure the physical security of its own locations where Personal Data is Processed. The spaces mainly include the company’s office space. The location has access controls, security cameras and alarms to prevent unauthorized access.Seidat also restricts access to Personal Data on Seidat’s own devices by implementing device encryption, password protection, and remote wipe capabilities. This ensures that Personal Data is protected even in the event of device loss or theft. Storing personal data in any format that cannot be encrypted or password-protected, like in printed format, is prohibited.Subprocessor’s locations where Personal Data is Processed must meet the industry standard requirements for physical security, like restrictions to only authorized personnel, and security measures such as security cameras, alarms and access controls.
7.3.6. Effectiveness of technical and organizational measures. Seidat regularly tests, assesses, and evaluates the effectiveness of our technical and organizational measures to ensure the security of the Processing of Personal Data. We conduct regular security audits and assessments to identify any potential vulnerabilities or weaknesses in our security measures.In addition, we regularly review and update our policies and procedures to ensure that they remain current and effective.Seidat also maintains incident response and business continuity plans to ensure that we can respond quickly and effectively in the event of a security incident or other disruptive event. Our personnel is trained to respond in a timely and effective manner.
7.3.7. System configuration. Seidat implements measures to ensure the security and integrity of our systems and processes, including our system configuration and default configuration settings. We follow best industry practices and standards to ensure that our systems are configured securely and that default configurations do not create vulnerabilities.We regularly review and update our system configuration settings to ensure that they are aligned with our security policies and procedures. We also maintain strict controls over changes to system configuration settings, ensuring that changes are documented, approved, and tested before they are implemented.Furthermore, our software development processes include secure coding practices, and we regularly assess and update our default configurations to ensure that they are secure and do not create potential vulnerabilities.
7.3.8. Internal IT. Seidat has implemented measures to ensure that our internal IT and IT security governance and management are aligned with best industry practices and standards. We have established an IT security governance framework that includes policies, risk assessments, procedures, and controls to ensure the ongoing security and integrity of our systems and processes.We regularly review and update our IT security governance framework to ensure that it remains current up-to-date and effective. This includes conducting regular risk assessments to identify potential security risks and vulnerabilities and implementing controls to mitigate those risks.Our management team is responsible for overseeing our IT security governance and management. Our management team includes experienced professionals who are trained in the latest security technologies and techniques.Furthermore, we conduct regular security awareness training for all Seidat personnel to ensure that they are aware of potential security risks and how to mitigate them. Our Employee Training Plan at Seidat includes topics such as password security, phishing prevention, and secure data handling. Training is typically conducted quarterly with a varying topic, with reviews biannually on its effectiveness. The COO or CEO is responsible for conducting training sessions.
7.3.9. Measures for ensuring deletion of Personal Data. Seidat understands the importance of ensuring the deletion of Personal Data when it is no longer needed or when requested by the Customer on behalf of a Data Subject. We have implemented measures to ensure that all Personal Data is securely and effectively deleted from our systems and processes upon termination of the Agreement.We have established clear guidelines and procedures for handling requests for deletion, and we ensure that Personal Data is securely deleted or anonymized when it is no longer needed for the purposes for which it was collected. This includes implementing secure deletion methods and tools to ensure that Personal Data is permanently deleted and cannot be recovered.